Imagine a community-wide discussion focused on ways to address an active shooter. A federal agency convenes federal and local law enforcement, emergency services, and representatives from the agency’s command, including human resources, information technology, a continuity of operations component, and their insider threat program. Imagine the different perspectives, agendas, and cultural norms which might emerge from this group.
This event took place in Washington, DC this year. Unlike their previous table-top exercises, this community practiced using a lens of Adaptive Space. A Forbes best business book of 2018, Adaptive Space outlines a framework for how leaders can successfully overcome any disruptive challenge.
Adaptive Space offers leaders a way to locate hidden areas of opportunity or strife that pose risks to an organization. For example, one way to mitigate insider threats involves looking at the lifecycle of employees’ experiences. Often this involves coordination between HR and security; while security policies are often black and white, HR policies have gray areas. Adaptive Space offers a way to broker these differences.
Instead of driving conflicting agendas or exaggerating adversarial relationships, we facilitated a series of exercises to demonstrate the essential need for this community to be connected before and after an event, not just during the event. Additional substantial steps emerged for how the community will address policies, procedures, and countermeasures.
The agency also realized the need to revise the mission and priorities of their insider threat program. This critical conversation gave them awareness about the need to develop a new discussion, agreement, engagement, action plan, and policy with other components within their organization.
With the utility of Adaptive Space, our customers are locating potential areas of conflict or contention. These leaders are gaining insight into trends such as revenue stagnation and decline in employee morale. For example, one leader recognized how a lack of the ability to innovate could lead to friction points.
In managing insider threats, best practice programs address the following areas and the risks associated with each:
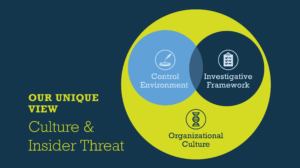
First line supervisors are most likely to see the lead indicators of a potential threat, as they are closest to staff. Without standard meeting procedures and reports for data analysis, and discussion across each relevant function and governing body, these risks are most often missed.
The Clearing recommends using the Adaptive Space framework to enable leadership and senior management to have critical conversations with members on the front lines.
Today organizations face two major challenges: to produce more, faster, and with fewer resources, and to maintain continuity of operations for customers. Technical implementations can only go so far as to address insider threats within this ecosystem. Our clients in federal agencies, the energy sector, and financial institutions struggle with the implementation and adoption of their insider threat programs. The pace of change is simply too disruptive.
Given the above, there is yet one other thing that makes insider threat programs fail. In our research, we have found that not one insider threat program addresses employee and contractor adoption from a human perspective. These organizations are investing millions of dollars and expert resources on policies, training, and procedures that do not always account for diverse human viewpoints. These insider threat programs are failing to achieve their adoption targets.
Would it be beneficial to hear what employees, management, and leadership are saying about your organization, in order to examine potential areas of friction? In a related blog, I talk about how our Cultural Assessments surface new insights about insider threat.
Ready to experience success through cultural adoption of your insider threat and risk program? Connect with me and let’s talk.
